Identity Vault
Identity Vault is an all-in-one frontend identity management system that combines security best practices and the latest in biometric authentication options for Ionic apps running on iOS and Android.
Don't have an Identity Vault subscription? Try it free now.
The Vault manages secure user identity and session tokens, ensuring sensitive data is encrypted at rest, stored only in secure locations on the device, and unlocked only with biometric identity (TouchID/FaceID). Always-on Session Management safeguards data even when not using your app, with background screen protection for sensitive data and apps, and automatic logout based on inactivity time.
Identity Vault is built and supported by Ionic's native mobile experts and includes ongoing updates and maintenance, including new API features, patches, updates, and compatibility upgrades for new iOS & Android releases.
Why Identity Vault?
Many frontend authentication workflows use unsecure practices like storing tokens unencrypted or using weak authentication logic that is easily compromised. In the past, Ionic developers have resorted to combining third party Cordova plugins, often resulting in insecure setups due to the lack of correct implementation of biometric and at-rest encryption strategies.
Common security mistakes include:
- Not implementing Apple and Google's mobile security best practices. Guidelines often change with each major operating system release.
- Combining disparate Cordova plugins together. While the code is open source, it's challenging to know if the latest security best practices are in place, and whether the plugin developer will keep them up to date.
- Leaking data. Storing tokens unencrypted in localstorage is common but data is easily accessible.
- Not clearing tokens after user inactivity or when new fingerprints are added. Removing tokens protects users in the event of a lost or stolen device.
- Displaying data when app is in the background. Highly sensitive data should be protected from shoulder surfing, especially if the mobile app is commonly used in public places.
Identity Vault handles all of the above and more, reducing your team's development time from weeks to minutes while eliminating the need to learn complex native APIs. Instead, they can focus on delivering business critical app features.
How It Works
Among Identity Vault's many features is the secure management of user identity and session tokens. The Vault ensures sensitive data is encrypted at rest, stored only in secure locations on the device, and unlocked only with biometric identity (TouchID/FaceID). Here's how it works in practice, in a typical authentication workflow.
An app user logs into your mobile app and the backend authentication system verifies their credentials. If valid, the system sends back a session token representing the user's identity and permissions. Since this token represents the ability to make changes on behalf of the user, it's crucial to secure it so that malicious persons or apps cannot access it.
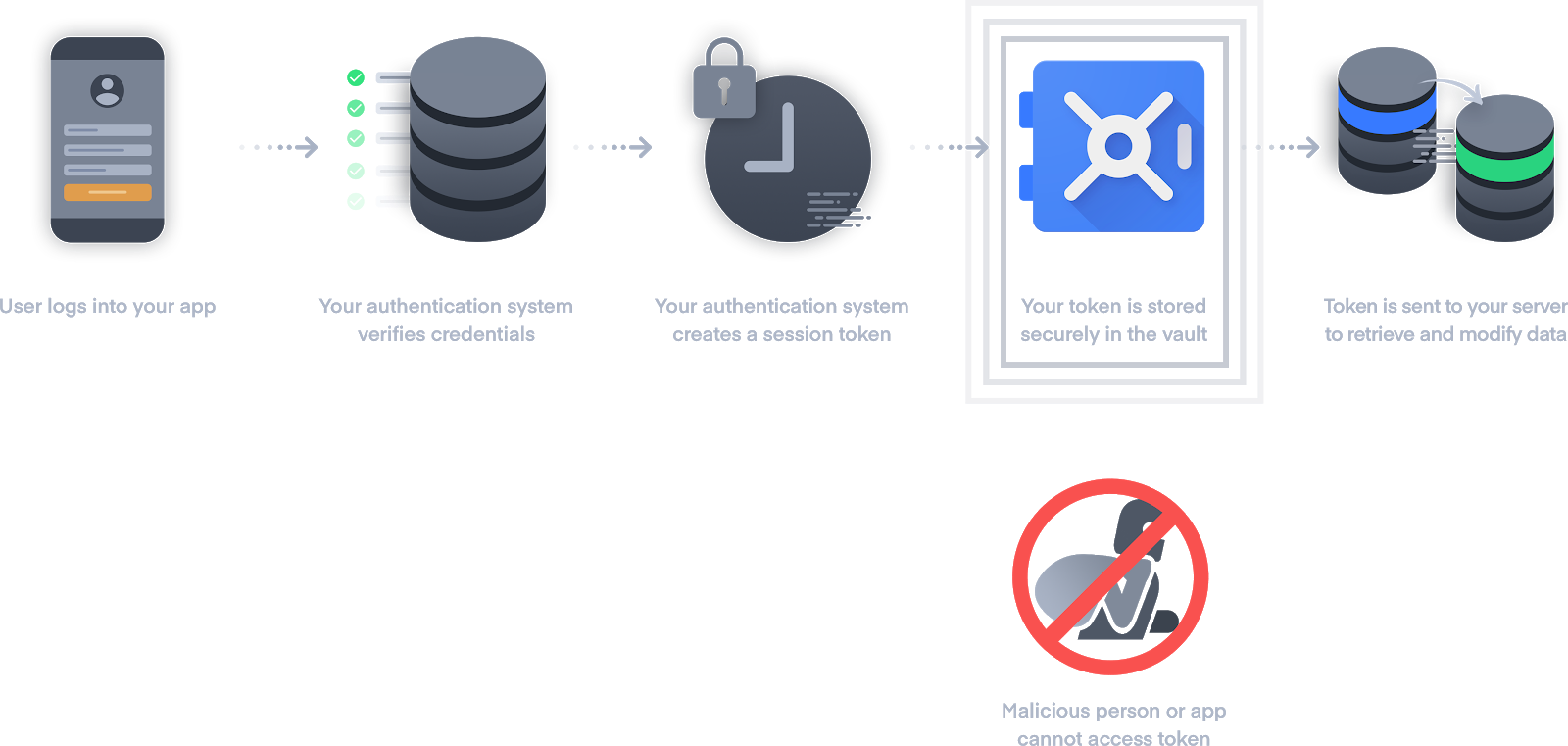
Your app must store the token somewhere so the user can continue to use it over time, as the token will be sent back to your server to retrieve and modify data at any time. This is where Identity Vault comes in. The token is encrypted and stored at-rest securely on a physical hardware chip - the Secure Enclave on iOS devices. The enclave is isolated from all other system components in order to ensure sensitive user data remains secure.
Later, when an attempt is made to retrieve the user token, the app prompts the user to authenticate using Touch ID or Face ID. After verification, it's permitted to get the token from the Secure Enclave and use it for subsequent data requests.
In addition to secure identity management, Identity Vault fully configurable session management. While in use, the auth tokens will be in-memory of your app, so for an additional layer of protection, the Vault will automatically lock based on the specified inactivity time. It also comes with screen protection, hiding your app's data when put into the background. On iOS, it uses your app's splash screen and the native hide system on Android. Finally, you can use Identity Vault's user service to add the auth token to every backend system request using a HTTP interceptor.
Reference Apps
While implementing Idenitity Vault, refer to these reference apps for examples showcasing all available security features.
Ready to secure your app? Install Identity Vault now.